VPC Interface Endpoints (powered by AWS Private Link) are a powerful technology to improve security and performance in an AWS environment. However, they come at a cost. In this article we will explore the VPC Interface Endpoints for AWS services and discuss how and when they should be used and before going to explain about VPC endpoints I would like to explain little bit about VPC.
What is Amazon Virtual Private Cloud (VPC)
Amazon Virtual Private Cloud (VPC) lets you provision a logically isolated section of the Amazon Web Services (AWS) Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including the selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
What is AWS Private Link
On November 8th, 2017, AWS Private Link was introduced as a way to connect to AWS Services like EC2, ELB and Kinesis Data Streams without traversing the public internet. Before Private Link, any API call to these services.
(eg. EC2:DescribeInstances or ELB:RegisterInstancesWithLoadBalancer) required an outbound internet connection – either a public IP address, NAT instance or NAT gateway. The request itself, including any sensitive information, would first leave your VPC and then travel across the internet to the AWS service you were calling.
With Private Link, these requests are routed over AWS’ internal networks instead. This obviously improves security. It also benefits performance, as laid out in this blog post by VMware Carbon Black.
On November 28th, 2017, AWS released the same functionality for customer and partner services. From this moment on, you can publish your own AWS-hosted application as a private service. This service can be consumed by other AWS accounts over AWS’ internal networks. The only requirement is that your application is fronted by a Network Load Balancer.
How does it work
To enable Private Link, you publish the Network Load Balancer in front of your application as a VPC Endpoint Service. When the endpoint service has been deployed, a service name will be displayed. This service name can be used by others to subscribe to your endpoint service.
When another AWS account subscribes to your endpoint service, they choose a subnet for every availability zone they want the service to be available in. AWS will deploy an Elastic Network Interface (ENI) in each of these subnets.
When an application in this AWS account tries to connect to your Network Load Balancer, traffic will be routed over these ENIs, through Amazon’s internal network, and to your NLB, without ever traveling over the public internet.
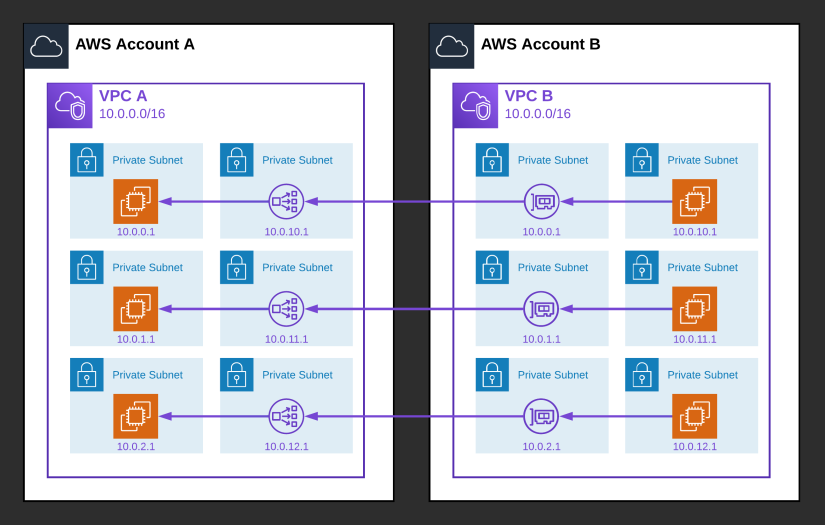
VPC Interface Endpoints for AWS Services
The exact same architecture is used to provide access to AWS service APIs like EC2, ELB, Kinesis, Secrets Manager, CloudWatch, and so on. Amazon has built these services around a Network Load Balancer – or has refactored existing services to use NLBs. The AWS News blog regularly posts articles like New – Use AWS PrivateLink to Access AWS Lambda Over Private AWS Network. Any time you see one of these, Amazon has migrated another service to use NLBs.
As AWS migrates more internal services to NLB, the list of services that support PrivateLink continues to grow. At the time of writing, there are 66 supported services, ranging from Amazon API Gateway to Amazon WorkSpaces, with notable mentions for security services like STS, KMS and CloudTrail.
Why use VPC Interface Endpoints
The two main reasons to use VPC Interface Endpoints are security and performance. Let’s look at these in turn.
Security: no internet traversal
The technical description above explains how any Private Link service uses Amazon’s internal networks to route traffic to its destination load balancer. This is useful for basic services like EC2 and ELB, but it becomes essential for security services like STS and Secrets Manager. These services are used to store and retrieve the most sensitive data types – passwords, usernames, API keys, temporary credentials, credit card info, and so on. The ability to guarantee this data will not traverse the internet is a big security win.
Security: VPC Endpoint Policies
Many of the AWS services with Private Link support also support Endpoint Policies. These IAM policies are applied on an existing AWS Interface Endpoint and determine which traffic can pass through the interface. This allows you to limit which operations and resources can be accessed from the VPC. For example, an Aurora endpoint can deny the DeleteDBCluster operation, or an Secrets Manager endpoint can only allow access to specific secrets. This solution protects against privilege escalation: even if a user would somehow gain access to the DeleteDBCluster permission, the command still wouldn’t pass through the interface endpoint.
More on VPC Endpoint Policies and how they can be used to protect against data exfiltration can be found on AWS VPC endpoint Policies
Performance: latency
Because the traffic over Private Link stays within Amazon’s networks, the physical distance travelled, the number of hops and the risk of traversing congested networks are all significantly lower. VMware Carbon Black ran performance tests on Private Link, and found an average latency reduction of about 70%.
Performance: bandwidth
Private Link supports a sustained bandwidth of 10 Gbps per availability zone with bursts up to 40 Gbps. If this is not enough, AWS support can increase this even further.
Performance: stability
The Carbon Black performance test also showed that using Private Link consistently lowers the number of errors and timeouts on high loads:
The results show that the VPC endpoint results in consistent timeouts errors and cannot reliably handle the load being applied, whereas the Private Link connection has minimal errors under the same load.
The balance of cost, security, and performance
With all the benefits mentioned above, I bet you’re jumping deploy VPC Interface Endpoints everywhere! However, there’s always a catch. In this case it’s an obvious one: cost. Amazon does not provide this service for free, and you should determine the value of using of using VPC Interface Endpoints for your workloads accordingly.
We will look at three scenarios below:
- A highly secure environment that only uses VPC endpoints and prohibits any outbound traffic over the internet
- A low security environment that uses no VPC endpoints
- A hybrid solution with public internet access and a few VPC endpoints
All pricing is based on the Ireland (eu-west-1) region.
High security
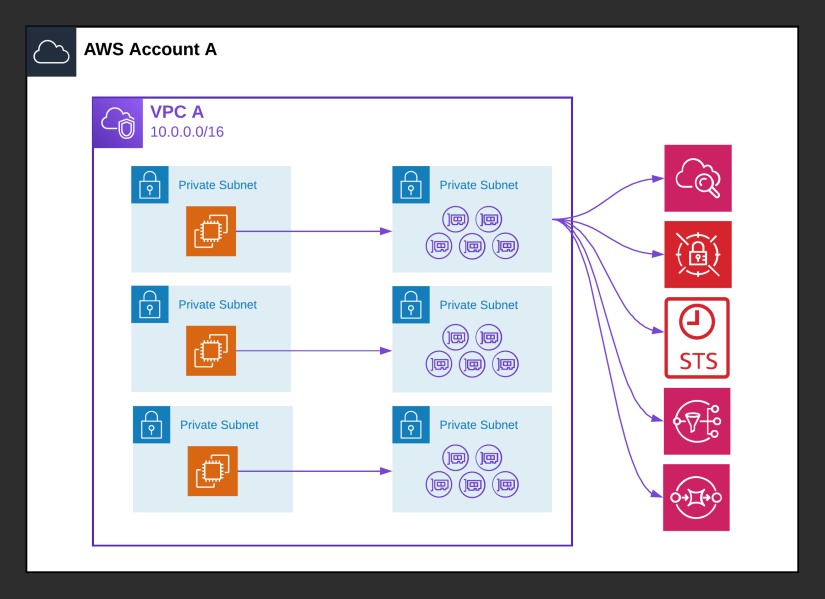
In a very sensitive environment, you want to guarantee that all AWS API calls stay within AWS’ networks and no data can be extracted to the internet. In this scenario, you will have no Internet Gateway and no NAT Gateway, so no outbound traffic is possible. However, this will also prohibit all interactions with AWS services, so you need VPC endpoints for every service you use.
In this example, your environment uses CloudWatch Logs, Secrets Manager, Security Token Service (STS), Simple Notification Service (SNS) and Simple Queue Service (SQS). The application is deployed in three AZs, so a total of 15 ENIs are deployed. The amount of data processed is very low, so will be set to 1 GB per ENI.
The cost to run the networking part of this solution is $120.06. From the PrivateLink pricing page:
- 730 hours in a month x 0.011 USD = 8.03 USD (Hourly cost for endpoint ENI)
- 1 GB per month x 0.01 USD = 0.01 USD (Private Link data processing cost)
- 8.03 USD + 0.01 USD = 8.04 USD (Hourly cost and data processing per endpoint ENI)
- 5 VPC endpoints x 3 ENIs per VPC endpoint x 8.04 USD = 120.60 USD (Total Private Link endpoints and data processing cost)
- Total Private Link endpoints and data processing cost (monthly): 120.60 USD
This might seem low, but keep in mind that this solution has no internet access, and every additional service the instances need to contact will cost an additional $24.12 per month.
Low security
In a more common scenario, contact with the public internet is not prohibited at all, and since all API calls use encryption in transit (HTTPS) anyway, customers are not worried about Secrets Manager or STS traffic traversing the internet. In this situation, NAT Gateway would be sufficient to protect private resources. We will deploy a NAT Gateway per availability zone for optimal redundancy.
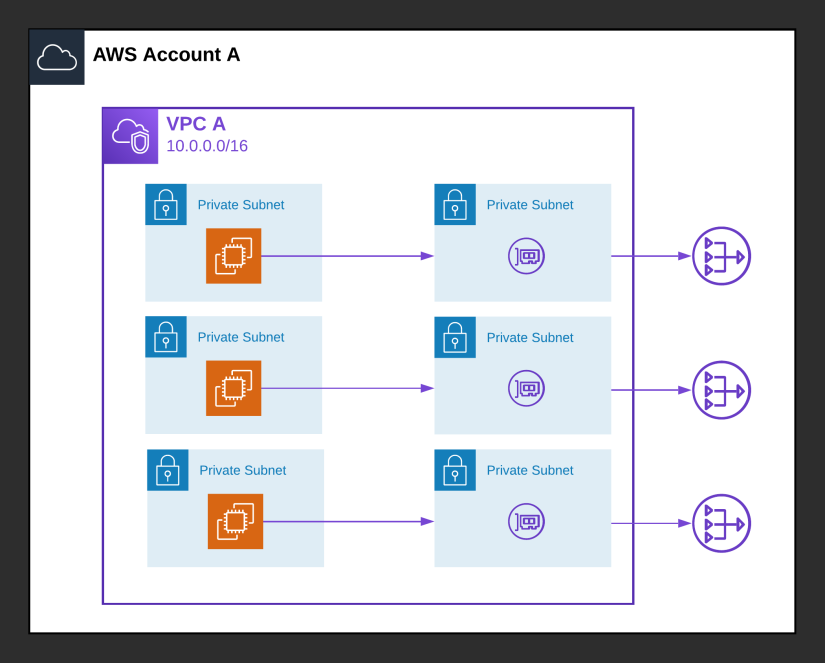
The cost to run the networking part of this solution is $105.27. From the VPC pricing page:
- 730 hours in a month x 0.048 USD = 35.04 USD (Gateway usage hourly cost)
- 1 GB per month x 0.048 USD = 0.05 USD (NAT Gateway data processing cost)
- 35.04 USD + 0.05 USD = 35.09 USD (NAT Gateway processing and month hours)
- 3 NAT Gateways x 35.09 USD = 105.27 USD (Total NAT Gateway usage and data processing cost)
- Total NAT Gateway usage and data processing cost (monthly): 105.27 USD
The cost of this solution is about 13% lower than the previous one, and this time the instances can connect to the internet. However, this solution provides no security benefits whatsoever.
Hybrid solution
Most workloads require some connection to the internet, for example to download security patches, connect to external APIs, or to send out metrics. For these purposes, NAT Gateways are the perfect solution. At the same time, you want to protect your sensitive information like access keys and STS tokens. In this case, you might want to deploy VPC Interface endpoints for your most sensitive AWS services, and route the rest over NAT Gateways. The diagram below depicts this hybrid scenario:
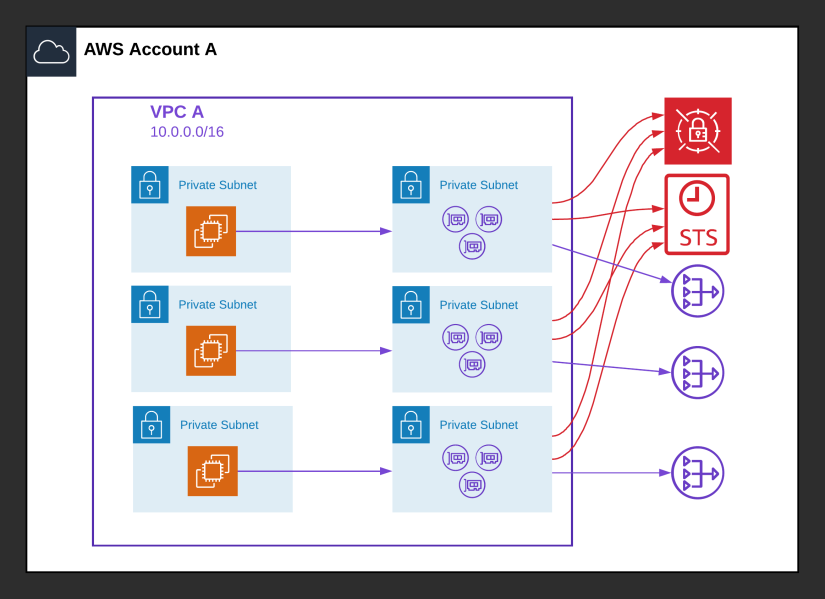
This is one of the most expensive solutions at $153.51, combining three NAT Gateways with two VPC Interface endpoints:
- 730 hours in a month x 0.011 USD = 8.03 USD (Hourly cost for endpoint ENI)
- 1 GB per month x 0.01 USD = 0.01 USD (PrivateLink data processing cost)
- 8.03 USD + 0.01 USD = 8.04 USD (Hourly cost and data processing per endpoint ENI)
- 2 VPC endpoints x 3 ENIs per VPC endpoint x 8.04 USD = 48.24 USD (Total PrivateLink endpoints and data processing cost)
- 730 hours in a month x 0.048 USD = 35.04 USD (Gateway usage hourly cost)
- 1 GB per month x 0.048 USD = 0.05 USD (NAT Gateway data processing cost)
- 35.04 USD + 0.05 USD = 35.09 USD (NAT Gateway processing and month hours)
- 3 NAT Gateways x 35.09 USD = 105.27 USD (Total NAT Gateway usage and data processing cost)
- Total PrivateLink + NAT Gateway and data processing cost (monthly): 153.51 USD
Hybrid solution (reduced redundancy)
Because of the high cost in the previous example, you might choose to run two NAT gateways instead of three. Of course, this means that when the NAT Gateway in the second AZ fails, you immediately lose two-thirds of your workload’s capacity, but this might be an acceptable risk.
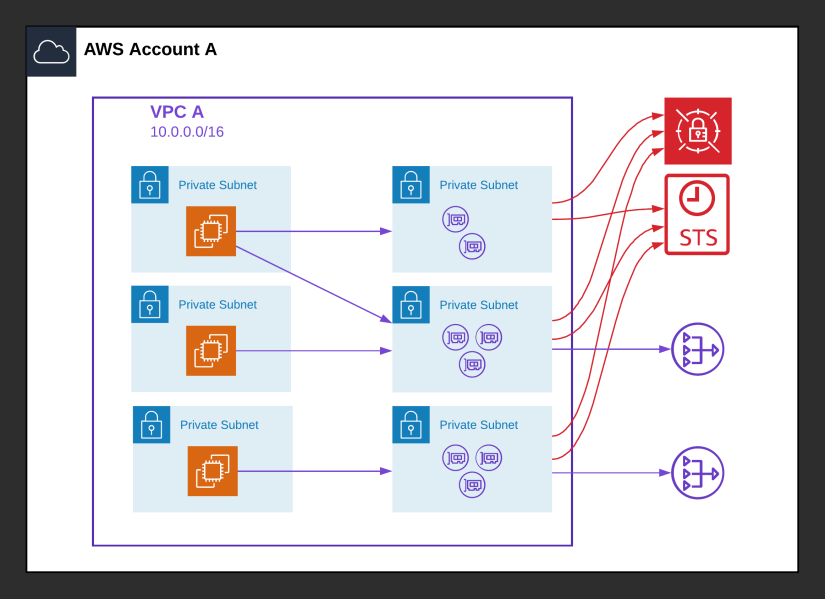
In this scenario, the cost will be reduced to $118.42.
- 730 hours in a month x 0.011 USD = 8.03 USD (Hourly cost for endpoint ENI)
- 1 GB per month x 0.01 USD = 0.01 USD (PrivateLink data processing cost)
- 8.03 USD + 0.01 USD = 8.04 USD (Hourly cost and data processing per endpoint ENI)
- 2 VPC endpoints x 3 ENIs per VPC endpoint x 8.04 USD = 48.24 USD (Total PrivateLink endpoints and data processing cost)
- 730 hours in a month x 0.048 USD = 35.04 USD (Gateway usage hourly cost)
- 1 GB per month x 0.048 USD = 0.05 USD (NAT Gateway data processing cost)
- 35.04 USD + 0.05 USD = 35.09 USD (NAT Gateway processing and month hours)
- 2 NAT Gateways x 35.09 USD = 70.18 USD (Total NAT Gateway usage and data processing cost)
- Total PrivateLink + NAT Gateway and data processing cost (monthly): 118.42 USD
VPC Gateway Endpoints
A special mention should go out to the older technology of VPC Gateway Endpoints. These endpoints are only available for S3 and DynamoDB. As the name implies, these endpoints are not deployed as an interface in a subnet, but instead as a route on your route tables. The functionality of Gateway Endpoints is the same as for Interface Endpoints, including their support for endpoint policies. However Gateway Endpoints are free. This little-known fact is buried all the way at the bottom of the VPC pricing page:
Note: To avoid the NAT Gateway Data Processing charge in this example, you could setup a Gateway Type VPC endpoint and route the traffic to/from S3 through the VPC endpoint instead of going through the NAT Gateway. There is no data processing or hourly charges for using Gateway Type VPC endpoints. For details on how to use VPC endpoints, please visit VPC Endpoints Documentation.
This means there is absolutely no reason not to use Gateway Endpoints, and they should be a standard component of every VPC deployment.
| Gateway VPC Endpoint | Interface VPC Endpoint | NAT Gateway | |
| Supported AWS services | S3, DynamoDB | some | all |
| Price per hour1 | free | $0.01 | $0.05 |
| Price per GB1 | free | $0.01 | $0.05 |
As you can see, using Gateway VPC Endpoints is cheaper than using Interface VPC Endpoint which is cheaper than using NAT Gateways
Saving potential: Depends on your traffic
Use the AWS PrivateLink pricing calculator to compute costs as per your requirements.
Example:
Let’s say that your current AWS infrastructure consists of a Lambda function that runs in your VPC, and that this Lambda transfers files to an S3 bucket at a rate of 100 GB/day.
Since the S3 bucket lives outside of your VPC, traffic originating from within your VPC must travel through your NAT Gateway to hit the public S3 bucket endpoint.
Your NAT Gateway costs for 1 day of this work is broken down into NAT Gateway Hourly Charge and NAT Gateway Data Processing:
| Category | Rate | Total (1 Day) |
| NAT Gateway Hourly Charge | $0.045 / Hour | $1.08 |
| NAT Gateway Data Processing | $0.045 / 1 GB | $4.50 |
| NAT Gateway Total | $5.58 |
In this scenario we want to create a VPC Gateway Endpoint in order to automatically route our VPC traffic via AWS PrivateLink to our S3 bucket.
Once the endpoint is created, traffic from our Lambda to our S3 bucket will get automatically routed via AWS PrivateLink without any futher configuration. Let’s look at the costs related to our new VPC Endpoint:
| Category | Rate | Total (1 Day) |
| VPC Endpoint Hourly Charge | $0.01 / Hour | $0.24 |
| VPC Endpoint Data Processing | $0.01 / 1 GB | $1.00 |
| VPC Endpoint Total | $1.24 |
So while we’ve introduced a new daily cost of $1.24, we’ve removed the Data Processing portion of our previous NAT Gateway cost estimate. Our new total cost for this work is:
| Category | Rate | Total (1 Day) |
| NAT Gateway Hourly Charge | $0.045 / Hour | $1.08 |
| NAT Gateway Data Processing | $0.045 / 1 GB | $0.00 |
| VPC Endpoint Hourly Charge | $0.01 / Hour | $0.24 |
| VPC Endpoint Data Processing | $0.01 / 1 GB | $1.00 |
| Solution Total | $2.32 |
When we compare the new $2.32 cost versus the previous $5.58 cost, we can see that adding a VPC Endpoint for our scenario has reduced our networking cost by 58% as well as improved security.
Conclusion
AWS Private Link for AWS services is an awesome and very powerful feature. It provides better security and performance, but cost depend upon business case scenario. Whether you should use them depends on your security requirements and budget.

One point to note here, VPC Interface endpoint supports 17 AWS managed services while Gateway endpoint supports only S3 & DynamoDB.
It is agreed that Interface endpoint has cost associated, but if Centralized architecture is used, then it becomes economical.
Also, it depends on the use case i.e if only the cost is priority and only S3 or DynamoDB needs to be used, then Gateway endpoints are suitable. But, if communication to other AWS managed services is considered along with Security and cost, then VPC interface endpoint seems to be a good fit.